Blogs

Aged Logins Analysis for Oracle E-Business Suite
Submitted by Skip Straus on 12 Oct, 2019 0 commentThis presents a User Responsibility Login Analysis aging report that analyzes when and how many times Oracle E-Business Suite (EBS) Users log on to their authorized Responsibilities. You create the aging buckets, and then count how many times the User logs in to each Responsibility in each of the buckets.
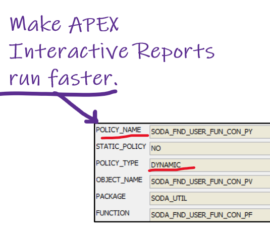
Dynamic WHERE Clause for APEX Interactive Reports and Grids
Submitted by Skip Straus on 17 Jul, 2019 1 commentAbsolute Technologies began converting our applications’ technical platform from Oracle Forms and Reports to Oracle Applications Express (APEX) several years ago. In doing so, we developed a proprietary platform for APEX that further accelerates application development and support, as well as providing built in reporting
Cash Receipts and Accessibility – An SoD Tale of Dependency
Submitted by Cam Larner on 17 Jun, 2019 0 commentWritten by Cam LarnerPresidentAbsolute Technologies, Inc. Earlier this year, a customer contacted me to report that SoD Violations Manager for Oracle E-Business Suite was inaccurately identifying that a user could perform transactions via the Receivables Cash Receipts form function, technically known as AR_ARXRWMAI_BATCH. She
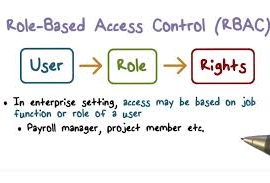
Blog Series: RBAC – What is it? Should you implement it?
Submitted by Cam Larner on 13 Feb, 2019 0 commentby Cameron LarnerPresidentAbsolute Technologies, Inc. Ever since the passage of Sarbanes-Oxley legislation, auditor scrutiny of ERP system user access controls at publicly traded enterprises has been evolving, as has corporate compliance. Though adoption has been slow, by now most public companies have either manual
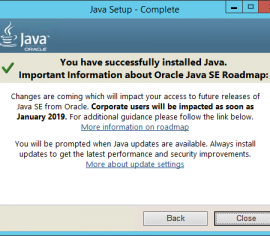
Oracle EBS – The 2018 Java SE warning for Corporate Users
Submitted by Cam Larner on 01 Nov, 2018 0 commentRecently, a customer’s Oracle EBS help desk staff member contacted us regarding his concern over a Java warning his users were receiving upon updating their Java desktop client. The Java message warning stated that come January 2019 “Corporate Users” access to future releases of Java SE will be impacted. I
