GRC and Audit Topics

Aged Logins Analysis for Oracle E-Business Suite
Submitted by Skip Straus on Sunday, 10/12/2019 - 9:32 pm 0 commentThis presents a User Responsibility Login Analysis aging report that analyzes when and how many times Oracle E-Business Suite (EBS) Users log on to their authorized Responsibilities. You create the aging buckets, and then count how many times the User logs in to each Responsibility in each of the buckets.
Read More
Blog Series: RBAC – What is it? Should you implement it?
Submitted by Cam Larner on Sunday, 02/13/2019 - 12:41 pm 0 commentby Cameron LarnerPresidentAbsolute Technologies, Inc. Ever since the passage of Sarbanes-Oxley legislation, auditor scrutiny of ERP system user access controls at publicly traded enterprises has been evolving, as has corporate compliance. Though adoption has been slow, by now most public companies have either manual
Read More
Role Based Access Controls in R12 – Pros & Cons
Submitted by Cam Larner on Sunday, 10/25/2018 - 6:37 pm 0 commentThinking of deploying User Management’s RBAC (Role Based Access Controls) in your EBS R12 instance? RBAC, in principle, has been touted as a best practice for efficiently achieving SoD compliance in systems prone to access risk. Advocates assert that once configured, it requires less effort to maintain and provision
Read More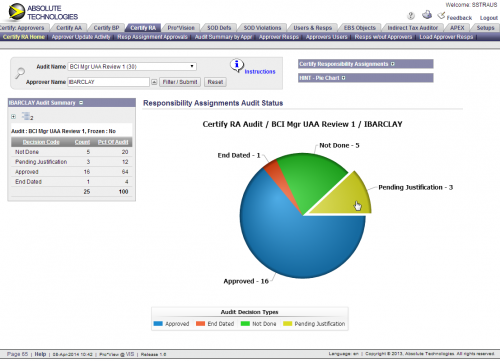
Certify Responsibility Assignments – Automate User Access Controls
Submitted by Cam Larner on Sunday, 03/15/2018 - 4:16 pm 2 commentsMany Oracle E-Business Suite customers periodically audit who has access to what EBS Responsibilities…manually! To automate user access controls in Oracle EBS, Absolute Technologies added Certify Responsibility Assignments™ (CRA) to its suite of GRC products. CRA empowers internal auditors and assignment approvers
Read More
OAUG Collaborate 18
Submitted by Cam Larner on Sunday, 03/15/2018 - 3:38 pm 0 commentAbsolute will be exhibiting at Booth 1344 during the OAUG Collaborate 18 conference from April 22-26, 2018 in Las Vegas at the Mandalay Bay Resort and Casino. Drop by to discuss how our suite of GRC solutions can automate your User Access Controls in E-Business Suite, from policy to certification, to achieve 100%
Read More